
Cyberoam Visibility & Control
Layer 7 policies and reporting, preventing data leakage and sophisticated application-layer threats
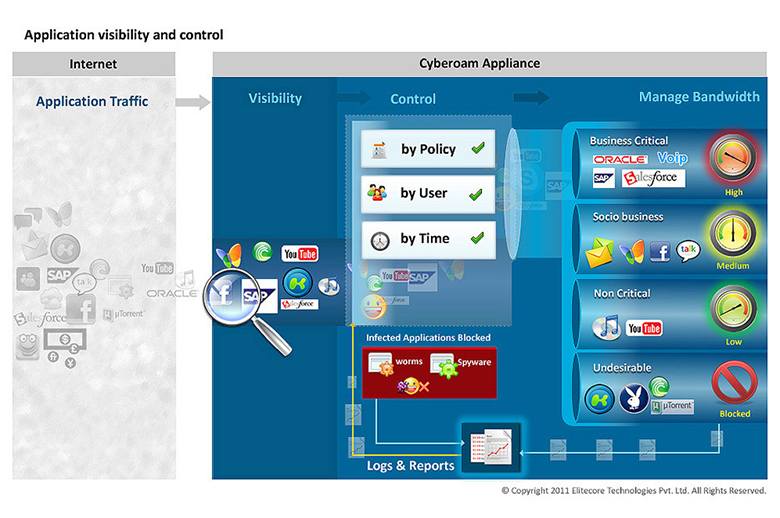
Cyberoam offers Application Visibility & Control with Layer 7 policies and reporting, preventing data leakage and sophisticated application-layer threats, including malware, phishing, botnets. The feature supports business applications, secure collaboration, Cloud and SaaS deployments with Layer 7 and Layer 8 identity-based policies.
Cyberoam Application Visibility & Control feature offers complete visibility on which applications are being accessed within the organization and by which user, irrespective of their ports and protocols. This stops sophisticated application-layer threats right at the network perimeter, ensuring Application Security. Based on network access policies, users and their job roles, and time, it offers application control to organizations to accelerate business-critical applications, stagger non-critical applications, selectively accelerate socio-business applications and block undesirable applications to achieve the twin goal of Application QoS and optimal bandwidth utilization. Real-time network logs and reports further allow organizations to promptly re-set network settings for maximum security and productivity.
| Feature | Feature Description | Benefit |
|---|---|---|
| Application Security |
|
|
| User and Time-based controls for Application Access |
|
|
| Bandwidth Control for Applications |
|
|
| Layer 8 Identity and Bandwidth-based Application Control |
|
|
