
Cyberoam CR500iNG-XP
Next-Generation Firewall for Enterprise Networks
Cyberoam – a Sophos Company, secures organizations with its wide range of product offerings at the network gateway. For the latest Cyberoam products, please visit our Sophos's store EnterpriseAV.com

Sorry, this product is no longer available, please contact us for a replacement.
Overview:
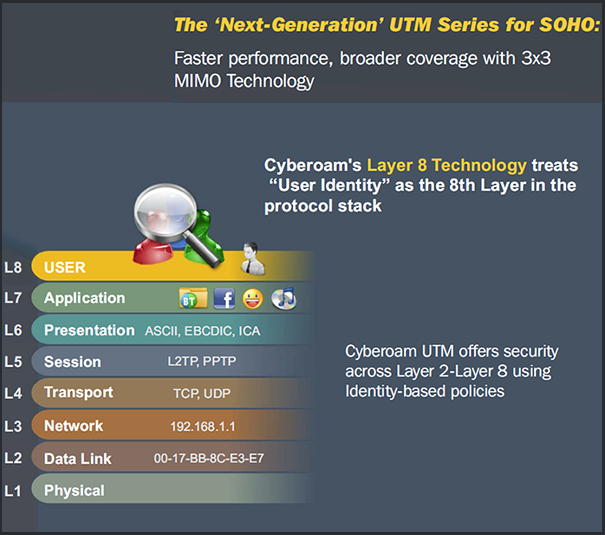
The mobilization of workforce has led to demand for anytime-anywhere access to network resources. This, along with increasing number of users like customers and partners connecting to an enterprise network from outside, and trends like rise in number of network users and devices, application explosion, virtualization, and more are leading to loss of security controls for enterprises over their networks. Cyberoam Next-Generation Firewalls (NGFW) with Layer 8 Identity-based technology offer actionable intelligence and controls to enterprises that allow complete security controls over L2-L8 for their future-ready security. Cyberoam’s Human Layer 8 acts like a standard abstract layer that binds with real Layers 2-7, enabling organizations to regain lost security controls.
Cyberoam CR500iNG-XP offers inline application inspection and control, website filtering, HTTPS inspection, Intrusion Prevention System, VPN (IPSec and SSL) and granular bandwidth controls. Additional security features like WAF, Gateway Anti- Virus, Anti-Spam are also available. The FleXi Ports (XP) available in CR500iNG-XP appliances offer flexible network connectivity with I/O slots that allow additional Copper/Fiber 1G/10G ports on the same security appliance.
Cyberoam security appliances offer high performance, assured Security, Connectivity and Productivity and an Extensible Security Architecture (ESA) for future-ready security in enterprises.
Next-Generation Firewall for Enterprises:
Offering Actionable Intelligence and Controls
| Cyberoam UTM features assure Security, Connectivity, Productivity | ||
|---|---|---|
|
|
|
Features:
The Cyberoam NGFWs offer next-generation security features to organizations to protect against newly-evolving threats.
|
|
|
|
|
|
|
|
Based on the need, Enterprises can get additional security features like Web Application Firewall, Gateway Anti-Virus, Gateway Anti-Spam, and more.
Specifications:
| Specification | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Interfaces
System Performance*
Stateful Inspection Firewall
Application Filtering
Intrusion Prevention System (IPS)
User Identity and Group Based Controls
Administration and System Management
|
User Authentication
On-Appliance Cyberoam-iView Reporting
Virtual Private Network
SSL VPN
Web Filtering
Bandwidth Management
Web Application Firewall
|
Gateway Anti-Virus & Anti-Spyware
Gateway Anti-Spam
Wireless WAN
Networking
High Availability
IPSec VPN Client******
Certification
Hardware Specifications
Compliance
Dimensions
Power
Environmental
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
#If Enabled, will bypass traffic only in case of power failure.
**Additional Purchase Required.
*Antivirus, IPS and UTM performance is measured based on HTTP traffic as per RFC 3511 guidelines. Actual performance may vary depending on the real network traffic environments.
Supports and Subscriptions:
Subscriptions:
- Antivirus and Anti Spam Subscription: Protection against Internet and mail based malware
- Comprehensive Value Subscription: Comprehensive Value Subscription includes Anti Malware, Anti Spam, Web and Application Filter, WAF, Intrusion Prevention System , 24x7 Support, hardware warranty and RMA fulfillment
- Gateway Anti Spam: Zero-hour protection with industry’s highest spam detection capabilities
- Gateway Anti Virus: Gateway level protection from viruses, worms and malicious code
- Intrusion Prevention System: Protects from intrusion attempts, DoS attacks, malicious code transmission, backdoor activity and blended threats
- Outbound Anti Spam: Protects service providers from recurring incidents of outbound spam in the network.
- Security Value Subscription Plus: Cyberoam Security Value Subscription Plus includes Anti Malware, Web and Application Filter, Intrusion Prevention System , 24x7 Support, hardware warranty and RMA fulfillment
- Security Value Subscription: Cyberoam Security Value Subscription includes Anti Malware, Web and Application Filter and Intrusion Prevention System, 8x5 Support, hardware warranty and RMA fulfillment
- Total Value Subscription Plus: Cyberoam Total Value Subscription Plus includes Anti Malware, Anti Spam, Web and Application Filter, Intrusion Prevention System, 24x7 Support, hardware warranty and RMA fulfillment
- Total Value Subscription: Cyberoam Total Value Subscription includes Anti Malware, Anti Spam, Web and Application Filter and Intrusion Prevention System, 8x5 Support, hardware warranty and RMA fulfillment
- Web and Application Filter: Dependable web and application filtering to control and report non-work and malicious web and network traffic activity.
- Web Application Firewall: Prevents exploitation of web applications vulnerabilities.
Supports
Basic 8x5 Support: 8x5 Phone, Email and Web Chat support with firmware upgrades , hardware warranty and RMA fulfillment
Premium Support 24x7: 24x7 Phone, Email and Web Chat support with firmware upgrades, hardware warranty and RMA fulfillment
| 8x5 Basic Support | 24x7 Premium Support | |
|---|---|---|
| Technical Support | ||
| Timings | 10AM - 6PM (Local Time Zone) | Anytime during the day |
| Web Based Support | Yes | Yes |
| Phone Based Support | Yes | Yes |
| Chat Based Support | Yes | Yes |
| Number of support incidents per annual subscription | Unlimited | Unlimited |
| First Response Time | 4 Hours | 1 Hour |
| Onsite Support Services* | - | Fee Based Service |
| Software Support | ||
| Software & OS Upgrades and Patches | Yes | Yes |
| Hot Fixes and Enhancement upgrades | Yes | Yes |
| Signature & database update | Yes | Yes |
| Hardware Warranty | ||
| Limited Hardware warranty & Replacement | Yes | Yes |
| Return and Replacement policy | 10 Days | 4 Days |
| Advanced Hardware Replacement | - | Yes |
| Customer Portal | ||
| Product Documentation and Guides | Yes | Yes |
| Technical Trainings - CCNSP & CCNSE Certifications | Fee Based | Fee Based |
| Online Demo | Yes | Yes |
| Version Release Notes | Yes | Yes |
| Support Renewals | ||
| One, two and three (1, 2 and 3) Year Renewals | Yes | Yes |
Download the Cyberoam Basic Support Plan Datasheet (PDF).
Download the Cyberoam Premium Support Plan Datasheet (PDF).
Documentation:
Download the Cyberoam CR500iNG-XP Datasheet (PDF).
Download the Cyberoam UTM Techsheet (PDF).
