 Cyberoam Central Console
Cyberoam Central Console
Central Security Control for MSSPs and Distributed Enterprises

Sorry, this product is no longer available, please contact us for a replacement.
Overview:
Distributed Threat Control
Zero-hour threats that spread to millions of computers within hours, outpacing traditional security solutions are threatening enterprise networks. Blended attacks in the form of viruses, worms, trojans, spyware, phishing, pharming are compromising networks through entry at the weakest points of enterprise infrastructure - remote and branch offices - that are generally not equipped to handle complex threats.
For geographically distributed networks of large enterprises and Managed Security Service Providers (MSSPs) that provide multiple security devices at distributed locations, this delays attack response across networks while offering poor visibility into remote network activity. The fact that remote offices and managed client networks do not have qualified technical manpower to handle attacks compounds the delay. All the same, enterprises struggle to implement, monitor and control a uniform security policy, raising security, productivity and legal issues. Hence, the ability to identify, impact and take rapid enterprise-wide action is a pre-requisite to enforcing distributed security. For MSSPs, the ability to implement a broad security policy across multiple clients simplifies operations while maintaining high security across client networks.
Cyberoam Centralized Threat Management
Cyberoam Central Console (CCC) offers coordinated defense against zero-hour and blended threats across distributed networks. It enables enterprise-wide implementation of corporate Internet polic configuration of an enterprise-wide security policy that strengthens branch and remote office security while lowering operational complexity. centralized, ies. Through configuration, enforcement of global policies as well as traffic scanning for Firewall, Intrusion Prevention System, Content-Filtering, Anti-virus and Anti-spam, CCC supports the configuration of an enterprise-wide security policy that strengthens branch and remote office security while lowering operational complexity.
CCClowers the operating cost of deploying, upgrading and maintaining multiple devices in the enterprise, offering complete control over distributed networks from the central office or the Security Operations Center (SOC) of MSSPs. CCC supports CR15i, CR25i, CR25ia, CR35ia, CR50i, CR50ia, CR100i, CR100ia, CR200i, CR300i, CR500i, CR1000i, Cr1500i.
Identity-Based Policy Implementation
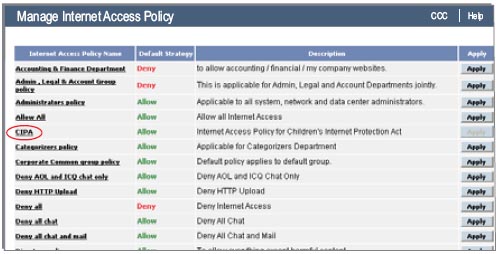
The CCC enables administrators to push work-profile based security policies to remote locations thus allowing implementation of enterprise wide standard security policy. This fully leverages Cyberoam's unique user identity-based security approach. The CCC also enables single point implementation of compliance measures for large enterprises and MSSPs. It is compliant across the board with CIPA, HIPAA, GLBA, PCI-DSS and SOx.
Alerts and Audit Logs
The CCC sends instant email alerts on device configuration changes taking place across distributed networks. This enables the administrator to take corrective actions for changes in device connectivity status, unchanged default passwords, change inCCCupdate repository, etc. The CCCalso provides audit logs to support configuration and policy changes on distributedCRdevices, support addition and removal of devices, create, modify and delete policies and rules and keep track of successful/unsuccessful log-in attempts. To view the audit log, administrators use appropriate data filters.
Features & Benefits:
| Features: | Benefits: |
|---|---|
| Centralized Configuration and Control |
|
| Device-Group Base Roles |
|
| Centralized Monitoring and Control |
|
| Centralized Policy Definition and Enforcement |
|
| Web Based Interface and Dashboard |
|
Screenshots:
Centralized Device Management
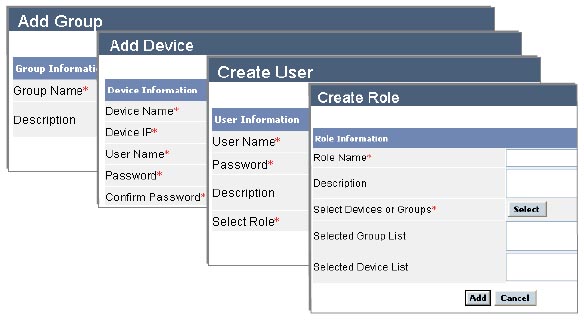
Cyberoam Central Console’s centralizedWeb GUI enables remote management of all distributed Cyberoam security devices including policy management, compliance enforcement, monitoring and control. Cyberoam's easy-to-deploy and configure central console manages the task of configuring remote groups, devices, users and roles in easy steps.
Easy Configuration using Web Interface
Policy Enforcement for Compliance
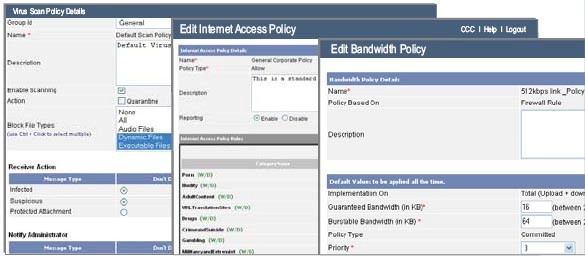
Policy flexibility to support business requirements
Create and implement enterprise-wide policies that are in accordance with corporate human resource guidelines to maintain the same levels of productivity and security measures across enterprise. MSSPs can apply differential policies across the different enterprises whose security they manage.
Centralized Policy Definition and Enforcement
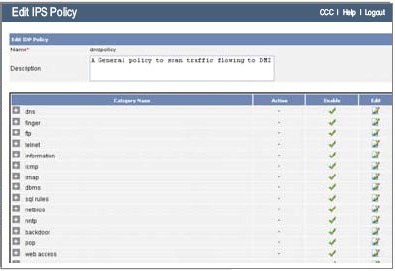
Instant enforcement of security policies in response to zero hour threats
Create and enforce Firewall rules, custom IPS policies using custom signatures to protect your enterprise from the latest threats, update remote Cyberoam devices from the Cyberoam Central Console and protect branch, remote or distributed offices with the same technical competency as the central location.
Centralized Firewall rule definition
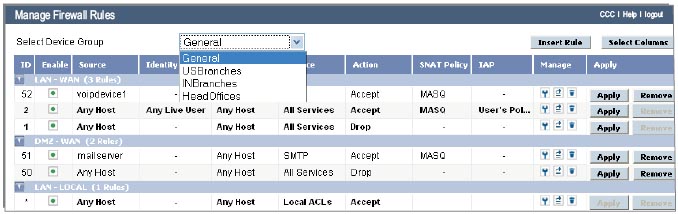
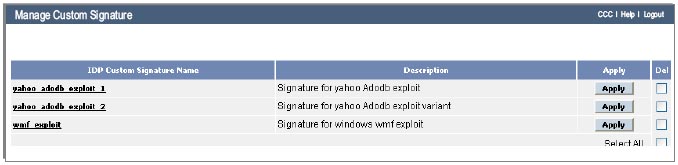
Custom IPS Signatures
Create custom IPS signatures and enforce them across the distributed networks for instant enterprise-wide security response to emerging threats.
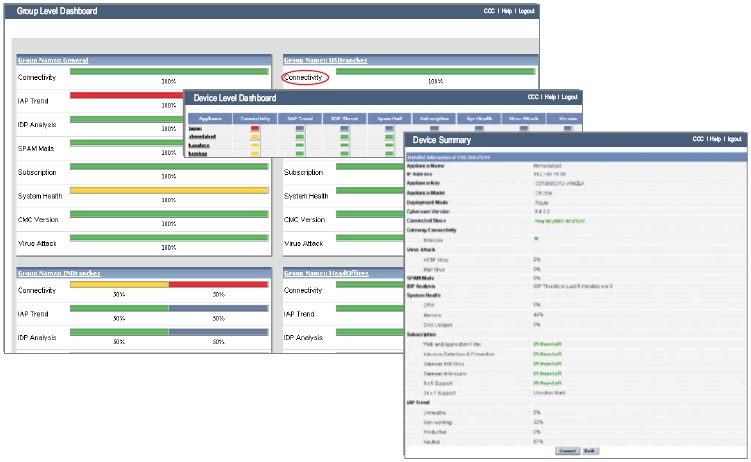
Instant enterprise-wide security visibility
Cyberoam Central Console enables central monitoring, ensuring instant action that provides uninterrupted security across networks. Monitor the remote and distributed offices through instant visibility into their network status. Take instant action by real time enforcement of security and firewall policies to control the attack
Deployment:
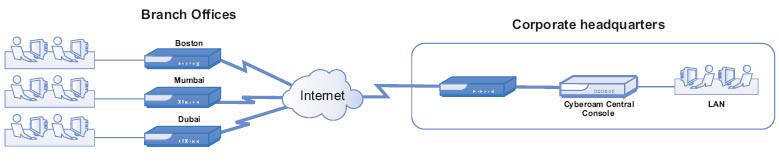
Cyberoam Central Console Deployment- MSSP
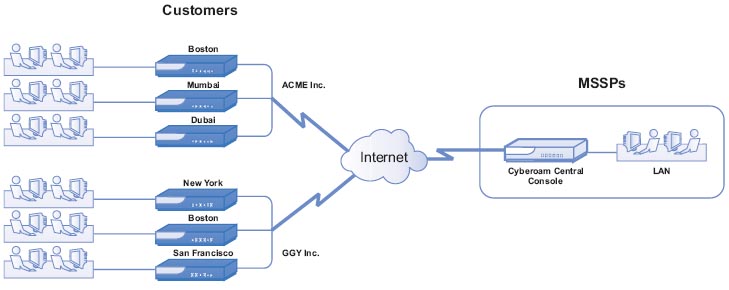
Cyberoam Central Console Deployment- Large Enterprise
Specifications:
| Technical Specifications: | CCC 15 | CCC 50 | CCC 100 | CCC 200 |
|---|---|---|---|---|
| Interfaces: | ||||
| 10/100/1000 GBE Ports | 6 | 6 | 6 | 6 |
| Console Ports (Rj45) | 1 | 1 | 1 | 1 |
| SFP (Mini GBIC) Ports | - | - | - | 2 |
| USB ports | 2 | 2 | 2 | 2 |
| Dimensions: | ||||
| H x W x D (inches) | 1.72 x 17.25 x 11.5 | 1.72 x 17.25 x 11.5 | 1.72 x 17.25 x 11.5 | 1.72 x 17.44 x 15.98 |
| H x W x D (cms) | 4.4 x 43.8 x 29.21 | 4.4 x 43.8 x 29.21 | 4.4 x 43.8 x 29.21 | 4.4 x 44.3 x 40.6 |
| Weight (kg, lbs) | 5.54, 12.188 | 5.54, 12.188 | 5.54, 12.188 | 6.04, 13.31 |
| Power: | ||||
| Input Voltage | 100-240 VAC | 100-240 VAC | 100-240 VAC | 100-240 VAC |
| Consumption | 128W | 128W | 128W | 185W |
| Total Heat Dissipation (BTU) | 375 | 375 | 375 | 475 |
| Environmental: | ||||
| Operating Temperature | 5 to 40 °C | 5 to 40 °C | 5 to 40 °C | 5 to 40 °C |
| Storage Temperature | 0 to 70 °C | 0 to 70 °C | 0 to 70 °C | 0 to 70 °C |
| Relative Humidity (Non condensing) | 10 to 90% | 10 to 90% | 10 to 90% | 10 to 90% |
| Cooling System (40mm Fan) | 3 | 3 | 3 | 3 |
| No. of CR Devices Supported | 15 | 50 | 100 | 200 |
Full Feature Set:
System Management
Administration
|
Centralized Remote Management
Real-time Monitoring
|
Upgrade Manager
|
Documentation:
Download the Cyberoam CCC Appliance Datasheet (PDF).
