Cyberoam Virtual Cyberoam CRiV-2C
Take Control of Your Security Infrastructure!
Cyberoam – a Sophos Company, secures organizations with its wide range of product offerings at the network gateway. For the latest Cyberoam products, please visit our Sophos's store EnterpriseAV.com

Sorry, this product is no longer available, please contact us for a replacement.
Overview:
Virtualization is taking organizations beyond the boundaries of their physical network infrastructure, empowering them to leverage their resources better and more flexibly, while quickly responding to the changing needs of their business. While higher efficiencies and lower total cost are few benefits of virtualization, security in virtual environments is an issue that organizations are struggling with, in the wake of virtualization!
Cyberoam Virtual UTM Appliances
Get complete control of your security infrastructure with Cyberoam virtual UTM appliances that offer industry-leading network security for your virtualized environments. Cyberoam virtual UTMs give you the flexibility to deploy a mix of physical and virtual appliances in your network, which can be managed centrally.
With the ability to scan all traffic in the virtual environment, Cyberoam virtual UTM protects virtual networks from attacks on hypervisor management console, hypervisor & Guest OS, virtualized web-facing applications and servers and allows organizations to secure Zero Trust Networks with its comprehensive security features in virtualized form.
Get a complete virtual security solution with Cyberoam virtual UTM, virtual Cyberoam Central Console and Cyberoam iView – Logging & Reporting software.
If you are an MSSP, reduce your operational and capital expenditure, and serve your customers better and at reduced costs, by having elastic network infrastructure utilization with virtualization.
If you are an SMB with virtual infrastructure, you can now extend your existing infrastructure to include security for your network without the need to add hardware security appliances, thus saving cost and time.
Take control of what you want, how much you want, how you want it, with Cyberoam virtual UTMs!
Benefits
- Security for dynamic virtual environments and Cloud
- Choice of individual or mixed virtual and physical network infrastructure
- Single virtual appliance to deploy and manage for comprehensive network security and single vendor to contact
- Easy scale-up of security infrastructure as business grows
- Deployment flexibility with licensing based on number of vCPUs
- Management and display of regulatory compliance
UTM Security features
- Stateful Inspection Firewall
- Gateway Anti-Virus and Anti-spyware
- Intrusion Prevention System
- Gateway Anti-spam
- Web Filtering
- Application Visibility & Control
- Web Application Firewall
- Virtual Private Network (VPN)
- IM Archiving & Controls
- Bandwidth Management
- On-Appliance Reporting
- Identity-based Security
WHAT you want
Virtual Security solution: Cyberoam virtual UTM appliances give complete control of security in virtual data-centers, Security-in-a-Box and Office-in-a- Box set-ups to organizations. Get comprehensive security in virtualized environments without the need for deploying a hardware security appliance anymore.
Support for infrastructure scale-up as the business grows: By providing a virtual network security solution to organizations and MSSPs, Cyberoam virtual UTMs allow security in virtual networks to be scaled up as the business needs of organizations/MSSP customers grow.
HOW MUCH you want
Easy Upgrade: Cyberoam virtual UTM appliances can be upgraded in no time and with maximum ease, using a simple activation key, to match the growing business needs of organizations/MSSP customers.
Benefit of shared infrastructure: By capitalizing on lean and peak periods of activities in the networks, organizations and MSSPs can optimize the resource utilization in their own/customer networks, using Cyberoam’s security in virtualized form.
HOW you want
Choice of Virtual and Physical Infrastructure: get the flexibility to choose between individual and a mix of physical and virtualized environments without worrying about security, with Cyberoam’s security solution for both physical and virtualized environments.
Deployment Flexibility: The licensing model for Cyberoam virtual UTM appliances is based on the number of vCPUs, giving deployment flexibility to organizations and MSSPs, unlike most competitor models that are based on concurrent sessions and number of users. Cyberoam virtual UTMs allow organizations to get maximum benefits of Cyberoam’s multi-core processing architecture by flexibly allotting vCPUs from the virtual infrastructure to the virtualUTMappliance.
No Hard Limits on Usage: If the number of network users in organizations or MSSP customer networks increase beyond the recommended number for a given model, Cyberoam virtual UTMs continue to secure these networks, allowing organizations and MSSPs to upgrade to a higher model only when they want to.
Features:
1.Protection for Virtualized networks
Inter-VM traffic scanning
External hardware security devices are incapable of scanning inter-VM traffic, creating blind spots in traffic within the virtualized environments. With their ability to scan Inter-VM traffic, Cyberoam virtual UTMs remove the network blind spots and allow granular firewall and security policies over inter-VMtraffic.
Hyperjacking & Hypervisor vulnerabilities
In cases where the hypervisor management console is placed in live production virtual environment due to lack of segmentation within virtual environments, the virtual networks are prone to attacks that exploit vulnerabilities on software layers like the hypervisor management console, hypervisor & Guest OS, putting the security of entire virtual network at risk.
Cyberoam virtual UTMs enable administrators to segment the hypervisor management console in DMZ and route all traffic through Cyberoam virtual UTM appliances. The Intrusion Prevention System on Cyberoam virtual UTMs scans Inter-VM traffic, VM to hypervisor traffic and ensures threat-free traffic. Web Application Firewall protection on Cyberoam virtual UTM blocks attacks that exploit vulnerabilities in the virtualized web applications.
Separation of duties
In case of external network security solutions, a level of Separation Of Duties (SOD) is achieved by default because the functions are hosted on separate physical systems that are managed and configured by separate teams. However, in case of collapsed DMZ, loss of SOD by default between security/network security and operations leads to security risks and potential conflict of interest between the roles.
Role-based administrator controls in Cyberoam virtual UTM allow separation of administrator duties. Cyberoam offers logs of administrator events and audit trails with its Layer 8 identity-based security and on-appliance reporting.
Zero Trust Networks
In an office-in-a-box setup, since the virtual infrastructure hosts the entire user workgroup, User-Identity based control and visibility becomes even more important.
Cyberoam’s Layer 8 Identity-based security policies over user authentication, service authorization and reporting (AAA) secure the Zero Trust virtual networks. Deployed at the perimeter or within the virtual infrastructure, Cyberoam virtual UTMs offer visibility and user-based access control in the virtualized environment. Ensure consistent security policy across your network – virtual and physical, with Cyberoam.
2.Comprehensive security:
Cyberoam virtual UTMs simplify the security for your virtual environments by consolidating multiple security functions in a single virtual appliance. Get all security features found in Cyberoam’s hardware appliances, viz. firewall, VPN, Gateway Anti-Spam, Gateway Anti-Virus, IPS, Web Application Firewall, Web Filtering, Application Visibility & Control and much more, to make your virtualized environments as secure as your physical network infrastructure.
3.Easy to deploy
Cyberoam virtual UTMs are easy to deploy with a licensing model that provides the flexibility to allot the number of vCPUs for Cyberoam virtual UTM based on your requirements. A simple key activation to upgrade to higher models and no hard limits on crossing recommended usage limits make Cyberoam virtual UTMs easy to deploy in your virtualized set-ups.
4.Compliance Management
In case of collapsed DMZs that hold sensitive information and office-in-a-box setup, compliance and privacy requirements become difficult to achieve, especially in a virtual environment. By segregating and securing traffic and data between and around your virtual entities, Cyberoam virtual UTMs help you stay regulatory compliant. The integrated logging and reporting feature offers in-depth reports of activities in your virtual infrastructure to support your organization to display compliance.
5.Centralized Management of Hardware and Virtual appliances
Centrally manage your physical and virtual infrastructure using a single interface with Cyberoam Central Console, available in hardware and virtual forms. Reduce the expense of separate management consoles for your physical and virtual environment needs as well as ensure centralized, consistent and quick security actions across your network.
Scenarios:
Cyberoam virtual UTMs offer security in the following set-ups:
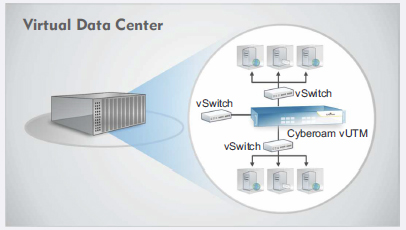 |
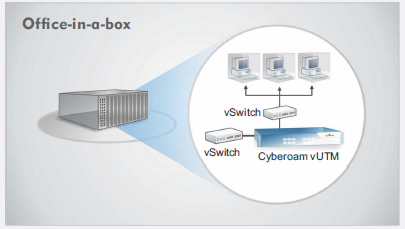 |
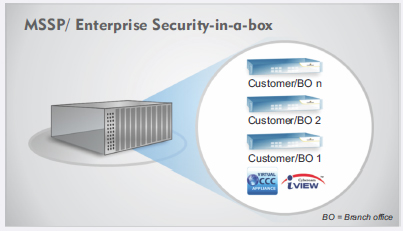 |
Specifications:
Cyberoam virtual UTM appliances give complete control of security in virtual data-centers, Security-in-a-Box or Office-in-a-Box set-ups, to organizations and MSSPs. With virtualized security appliance for virtual environments, Cyberoam enables scanning of inter-VM traffic, allowing granular firewall and security policies over inter-VM traffic, and offers comprehensive network security in virtualized environments to organizations without the need for deploying a hardware security appliance anymore. Cyberoam virtual UTMs allow organizations and MSSPs to optimize the resource utilization in their own/customer networks by capitalizing on lean and peak periods of activities in the networks.
Cyberoam’s licensing model for its virtual UTM appliances is based on the number of vCPUs, that gives deployment flexibility to organizations and MSSPs, unlike most competitor models that are based on concurrent sessions and number of users. Organizations get maximum benefits of Cyberoam’s multi-core processing architecture with virtual UTM appliances by flexibly allotting vCPUs from the virtual infrastructure to the virtual UTM appliance. With an easy upgrade feature using a simple activation key, organizations and MSSPs can match the growing needs of their business and customers in no time.
| Specification | ||
|---|---|---|
Stateful Inspection Firewall Gateway Anti-Virus & Anti-Spyware - Cyberoam Virus, Worm, Trojan Detection and Removal Gateway Anti-Spam - Cyberoam Inbound/Outbound Scanning Intrusion Prevention System - Cyberoam Signatures: Default (4500+), Custom Web Filtering - Cyberoam Inbuilt Web Category Database Application Filtering - Cyberoam Inbuilt Application Category Database |
Web Application Firewall - Positive Protection model Virtual Private Network - IPSec, L2TP, PPTP SSL VPN - TCP & UDP Tunneling Instant Messaging (IM) Management - Yahoo and Windows Live Messenger Bandwidth Management - Application and User Identity based Bandwidth Management User Identity and Group Based Controls - Access time restriction Networking - Automated Failover/Failback, Multi-WAN |
High Availability* - Active-Active Administration & System Management -Web-based configuration wizard User Authentication - Internal database Logging/Monitoring - Graphical real-time and historical Monitoring On-Appliance Cyberoam-iView Reporting - Integrated Web-based Reporting tool - IPSecVPNClient** - Inter-operability with major IPSec VPN Gateways Certification - ICSA Firewall - Cyberoam Corporate |
* Additional Purchase Required
Needs e1000/e1000e drivers emulation
| Technical Specifications | |||||
|---|---|---|---|---|---|
| CRiV-1C | CRiV-2C | CRiV-4C | CRiV-8C | CRiV-12C | |
| Hypervisor Support | Vmware ESx/ESxi 4.0/4.1/5.0, VMware Workstation 7.0/8.0/9.0, VMware Player 4.0/5.0, Microsoft Hyper-V 2008/2012 | ||||
| vCPU Support (Min / Max) | 1 / 1 | 1 / 2 | 1 / 4 | 1 / 8 | 1 / 12 |
| Network Interface Support (Min / Max) | 3 / 10 | 3 / 10 | 3 / 10 | 3 / 10 | 3 / 10 |
| Memory Support (Min / Max) | 1 GB / 4 GB | 1 GB / 4 GB | 1 GB / 4 GB | 1 GB / 4 GB | 1 GB / 4 GB |
| System Performance* | |||||
| CRiV-1C | CRiV-2C | CRiV-4C | CRiV-8C | CRiV-12C | |
| Firewall Throughput (UDP) (Mbps) | 1,500 | 3,000 | 3,500 | 4,000 | 4,000 |
| Firewall Throughput (TCP) (Mbps) | 1,200 | 2,500 | 3,000 | 3,500 | 4,000 |
| New sessions/second | 25,000 | 30,000 | 40,000 | 50,000 | 60,000 |
| Concurrent sessions | 230,000 | 525,000 | 1,200,000 | 1,500,000 | 1,750,000 |
| IPSec VPN Throughput (Mbps) | 200 | 250 | 300 | 350 | 400 |
| No. of IPSec Tunnels | 200 | 1,000 | 1,500 | 2,000 | 2,500 |
| SSL VPN Throughput (Mbps) | 300 | 400 | 550 | 550 | 750 |
| WAF Protected Throughput (Mbps) | 300 | 500 | 800 | 1,400 | 1,550 |
| Anti-Virus Throughput (Mbps) | 900 | 1,500 | 2,000 | 2,200 | 2,450 |
| IPS Throughput (Mbps) | 450 | 750 | 1,200 | 1,800 | 1,900 |
| UTM Throughput (Mbps) | 250 | 450 | 1,000 | 1,400 | 1,550 |
| Authenticated Users/Nodes | Unlimited | Unlimited | Unlimited | Unlimited | Unlimited |
| * Antivirus, IPS and UTM performance is measured based on HTTP traffic as per RFC 3511 guidelines. Actual performance may vary depending on the real network traffic environments. | |||||
Supports and Subscriptions:
Subscriptions:
- Antivirus and Anti Spam Subscription: Protection against Internet and mail based malware
- Comprehensive Value Subscription: Comprehensive Value Subscription includes Anti Malware, Anti Spam, Web and Application Filter, WAF, Intrusion Prevention System , 24x7 Support, hardware warranty and RMA fulfillment
- Gateway Anti Spam: Zero-hour protection with industry’s highest spam detection capabilities
- Gateway Anti Virus: Gateway level protection from viruses, worms and malicious code
- Intrusion Prevention System: Protects from intrusion attempts, DoS attacks, malicious code transmission, backdoor activity and blended threats
- Outbound Anti Spam: Protects service providers from recurring incidents of outbound spam in the network.
- Security Value Subscription Plus: Cyberoam Security Value Subscription Plus includes Anti Malware, Web and Application Filter, Intrusion Prevention System , 24x7 Support, hardware warranty and RMA fulfillment
- Security Value Subscription: Cyberoam Security Value Subscription includes Anti Malware, Web and Application Filter and Intrusion Prevention System, 8x5 Support, hardware warranty and RMA fulfillment
- Total Value Subscription Plus: Cyberoam Total Value Subscription Plus includes Anti Malware, Anti Spam, Web and Application Filter, Intrusion Prevention System, 24x7 Support, hardware warranty and RMA fulfillment
- Total Value Subscription: Cyberoam Total Value Subscription includes Anti Malware, Anti Spam, Web and Application Filter and Intrusion Prevention System, 8x5 Support, hardware warranty and RMA fulfillment
- Web and Application Filter: Dependable web and application filtering to control and report non-work and malicious web and network traffic activity.
- Web Application Firewall: Prevents exploitation of web applications vulnerabilities.
Supports
Basic 8x5 Support: 8x5 Phone, Email and Web Chat support with firmware upgrades , hardware warranty and RMA fulfillment
Premium Support 24x7: 24x7 Phone, Email and Web Chat support with firmware upgrades, hardware warranty and RMA fulfillment
| 8x5 Basic Support | 24x7 Premium Support | |
|---|---|---|
| Technical Support | ||
| Timings | 10AM - 6PM (Local Time Zone) | Anytime during the day |
| Web Based Support | Yes | Yes |
| Phone Based Support | Yes | Yes |
| Chat Based Support | Yes | Yes |
| Number of support incidents per annual subscription | Unlimited | Unlimited |
| First Response Time | 4 Hours | 1 Hour |
| Onsite Support Services* | - | Fee Based Service |
| Software Support | ||
| Software & OS Upgrades and Patches | Yes | Yes |
| Hot Fixes and Enhancement upgrades | Yes | Yes |
| Signature & database update | Yes | Yes |
| Hardware Warranty | ||
| Limited Hardware warranty & Replacement | Yes | Yes |
| Return and Replacement policy | 10 Days | 4 Days |
| Advanced Hardware Replacement | - | Yes |
| Customer Portal | ||
| Product Documentation and Guides | Yes | Yes |
| Technical Trainings - CCNSP & CCNSE Certifications | Fee Based | Fee Based |
| Online Demo | Yes | Yes |
| Version Release Notes | Yes | Yes |
| Support Renewals | ||
| One, two and three (1, 2 and 3) Year Renewals | Yes | Yes |
Download the Cyberoam Basic Support Plan Datasheet (PDF).
Download the Cyberoam Premium Support Plan Datasheet (PDF).
Documentation:
Download the Cyberoam Virtual UTM Brochure (PDF).
Download the Cyberoam Virtual UTM Tech Spec (PDF).
