 Cyberoam iView
Cyberoam iView
Intelligent Logging & Reporting Solution

Sorry, this product is no longer available, please contact us for a replacement.
 Overview:
Overview:
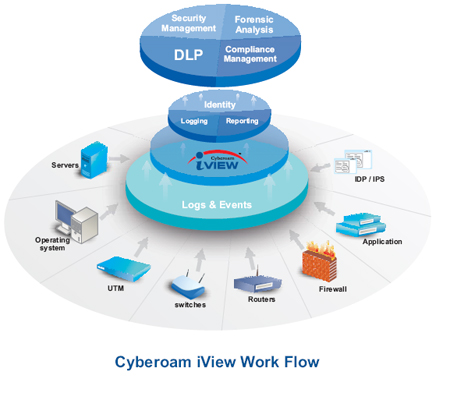
Cyberoam iView is an intelligent logging and reporting appliance that offers visibility into activity within the network by aggregating information from multiple devices that may be spread across multiple geographical locations, in near real-time. It offers multiple reports on iView's single dashboard, giving organizations an uninterrupted view of multiple network parameters like user, host, source, destination, protocol and more. Aggregated reporting gives them an organization-wide security picture, enabling them to apply or correct security policies from the central location.
The appliance-based approach provides simplicity in deployment and security that is difficult to achieve in a software solution. Its on-appliance storage offers data redundancy and faster data retrieval, supporting compliance requirements.
Organizations receive detailed drill-down reports through iView with a clear view of users and their activities over any device and location. Identity-based attack reports like top attacks, top applications used by attackers, top spam recipients, top viruses and more allow them to locate the weak link in the system, allowing quick problem identification and resolution while meeting the requirements of regulatory compliance. Host, application and firewall rule-based usage reports give identity-based information like top users consuming maximum bandwidth for uploads and downloads, top applications used, top accept and deny rules, allowing organizations to manage their resources and plan for their future needs in addition to enhance security levels.
Cyberoam iView supports proprietary devices as well as emerging network and security technologies, eliminating the need for separate logging and reporting solutions for different products within the system.
Key Highlights:
- Compatible with Wide Range of Devices – Cyberoam iView appliances enable organizations to store logs and reports of a range of devices, including UTMs, Proxy Firewalls, Custom Applications and any Syslog-compatible devices.
- Terabyte Storage Space – The appliances carry terabyte storage space to archive logs and reports of organizations across distributed locations.
- Data Redundancy – Cyberoam iView appliances use RAID technology to offer redundancy and high levels of storage reliability for organizations, ensuring appliance safety in the event of a hard disk failure.
- Commercial Support – The appliances carry commercial 8x5 and 24x7 support over telephone, chat and email in addition to annual maintenance contracts.
Features & Benefits:
Centralized Log Management
Analyzing logs is complex and time-consuming as multiple devices lead to management of various systems and proprietary technologies that deliver logs in different formats. iView allows effortless, identity-based log management in near real-time. Organizations can match user identity-based information contained in logs with their rights to reveal discrepancies in user activities.
Security Management
Use of multiple network devices, applications and protocols in organizations has increased the complexity of threats exponentially. A quick glance at the ard, its drilldown reports and identity-based logging and reporting enables organizations to instantly locate network attacks, their source and destination, allowing rapid action.
Storage Management
By utilizing the RAID technology, iView addresses the performance limitations of the conventional disk storage and delivers increased data protection against data loss due to the hard disk failure, high performance and increased storage capacity.
iView enables rapid event investigation and easy access to all audit and events data by storing raw logs and related records on the same appliance in a secure database. The database design aids both efficient storage and fast retrieval of the collected data. And, with the on-appliance terabyte storage space , iView appliances enable long-term, fully-accessible data retention.
Compliance Management
Regulatory compliance demands overwhelming effort, time and cost to retrieve and store logs and reports from various devices. iView eliminates compliance complexities with one-step access to critical information with multiple summery reports on a single dashboard that can be drilled down up to the third-level for granular information. Organizations can easily monitor access and security violations in the network, accelerating incident response and facilitating compliance.
Security breaches result in huge legal costs and loss of reputation that can drive organizations to bankruptcy. iView helps organizations reconstruct the sequence of events that occurred at the time of security breach through iView logs and reports. It helps reducing the cost of investigation and analysis and minimize network downtime while gathering historical information.
Sample Reports:
 Main Dashboard |
 Device Dashboard |
 iView Dashboard |
 Audit Log |
 Application Groups |
 Top Attacks |
 Blocked Attempts |
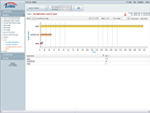 Top Spam Applications |
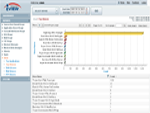 Top Viruses |
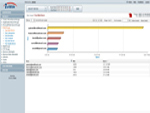 Top Web Users |
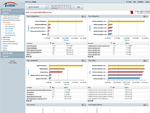 Web Usage by User |
 Top Mail Senders |
Technical Specifications:
| Hardware Specifications: | CR-iVU25 | CR-iVU100 | CR-iVU200 |
|---|---|---|---|
| Storage: | |||
| Total Available Storage | 500GB | 3.5TB | 7TB |
| Number of Hard Drives | 2 (500GB each) | 8 (500GB each) | 8 (1TB each) |
| Total Hard Drive Capacity | 500GB/R1 | 1.5 TB/R5 | 3TB/R5 |
| RAID storage Management | RAID 1 | RAID 5 | RAID 5 |
| Performance: | |||
| Events per Second (EPS) | 250 | 1000 | 2000 |
| Devices recommended | 25 | 100 | 200 |
| Interfaces: | |||
| Ethernet Ports (GBE) | 4 | 4 | 4 |
| Memory | 2GB | 4GB | 4GB |
| Console Ports | 1 (RJ45) | 1 (DB9) | 1 (DB9) |
| USB Ports | 1 | Dual | Dual |
| DVD-RW | No | Yes | Yes |
| VGA | No | Yes | Yes |
| Dimensions: | |||
| H x W x D (inches) | 1.72 x 10.83 x 17.32 | 3.46 x 16.7 x 20.9 | 3.46 x 16.7 x 20.9 |
| H x W x D (cms) | 4.4 x 27.5 x 44 | 8.8 x 42.4 x 53.1 | 8.8 x 42.4 x 53.1 |
| Weight | 3.78kg, 8.35lbs | 16 kg, 36lbs | 16 kg, 36lbs |
| Power: | |||
| Input Voltage | 100-240 VAC | 100-240 VAC | 100-240 VAC |
| Consumption | 65W | 265W | 265W |
| Total Heat Dissipation (BTU) | 175 | 425 | 425 |
| Environmental: | |||
| Operating Temperature | 5 to 40 °C | 5 to 40 °C | 5 to 40 °C |
| Storage Temperature | 20 to 70 °C | 20 to 70 °C | 20 to 70 °C |
| Relative Humidity (Non condensing) | 20 to 70% | 20 to 70% | 20 to 70% |
Full Feature Set:
Logs Reports
Reports
|
Administration
Operating Environment
|
Supported Web Browsers
Supported Network and Security Devices
|
Documentation:
Download the Cyberoam iView Appliance Datasheet (PDF).
